We bring the required subject expertise
IN YOUR INFORMATION SECURITY, PRIVACY & IT GRC JOURNEY
A wide group of CIO & IT Professionals consider the following as the top concerns related to impact of a cyberattack on their respective organization.
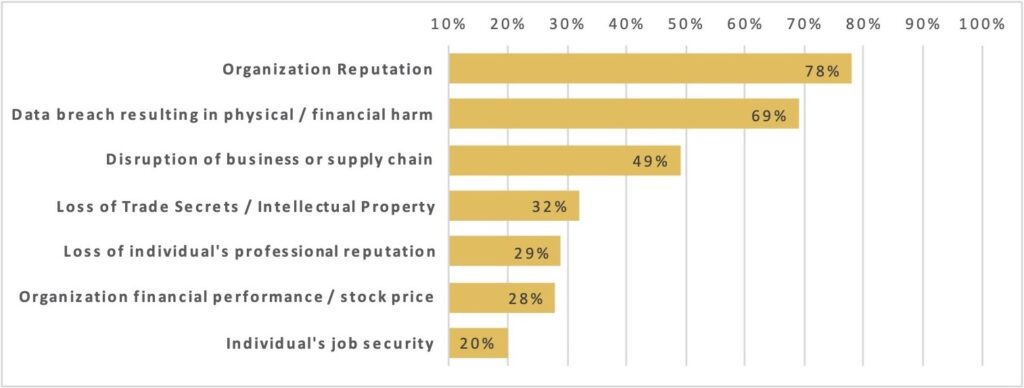
What’s yours?
OUR CONsulting solutions

IT Governance Services
COBIT 2019 & 5 Based Assessments
COBIT 5 to 2019 Upgrade Advisory
COBIT Trainings

ISO Certification Consulting
ISO 27001 Advisory
ISO 27701 Advisory
ISO 27018 Advisory
ISO 20000 Advisory
ISO 22301 Advisory
ISMS & PIMS Maintenance Services

Regulatory Compliance Assistance
IT General Controls Advisory
SOC 1, SOC 2 & SOC 3 Advisory
NESA Compliance Advisory
SAMA Compliance Advisory

Compliance Services
GDPR Advisory & Assessment
EU-US & SWISS-US Privacy Shield Advisory
HIPAA Advisory
PCI DSS Advisory
Managed Compliance Service
Why Us?
5 Reasons to choose us
- We understand the Business context of your project
- We are organisational change management experts
- We are subject matter experts in Governance & management of IT
- We provide Consultants, and not only Subject Matter Experts
- Our consultants are well groomed, and best-of-breed
Our consultants
- Ex-Big4 consultants
- Global management consulting practice leaders
- Ex-CTO, CIO’s
- Lead Auditors & Implementers
- Subject Experts & Practitioners