Man-in-the-Middle Attacks: Understanding & Preventing Cyber Threats
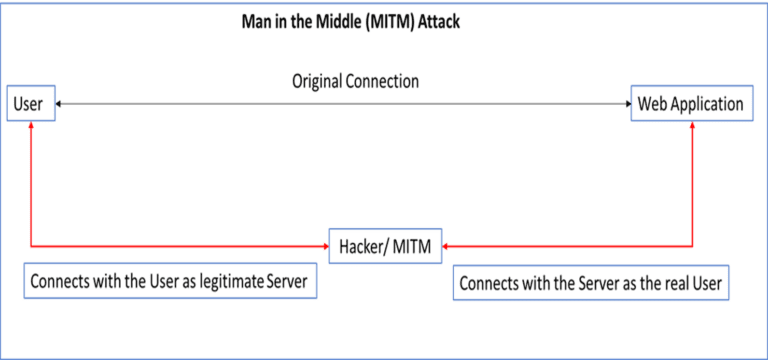
A MITM attack takes place when a communication between two systems is intercepted by an outside entity and it usually happens in any form of online communication such as, email, social media, web surfing etc. In this common type of security attack, the hackers try to eavesdrop on an individual’s private conversation and also target all the information inside his device.